Why HTTPS is important & how to make your website support it
Jul 6, 2019 18:10 · 1411 words · 7 minute read
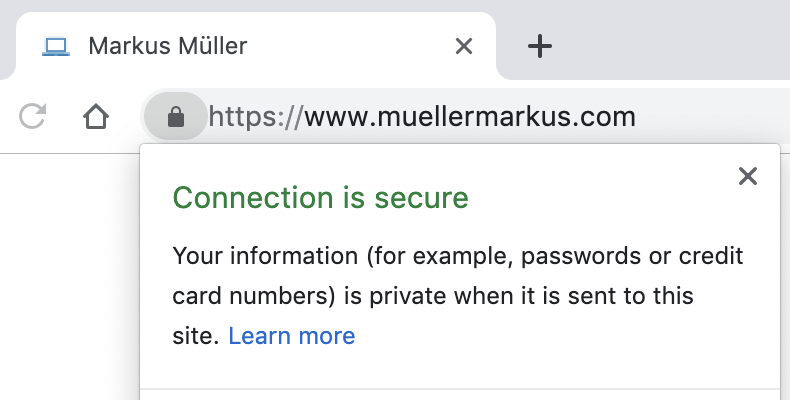
If you browse the web often, you have probably seen the “This connection is private” notice that gets displayed in your browser’s URL bar more and more often. This signalizes that you are connected to the website via HTTPS, which means the website is using authorized SSL certificates to encrypt your connection with the website, i.e. making it private. But why do websites use HTTPS?
I have structured my post in three parts:
- First, I will explain why HTTPS is important for a website’s users
- Then, I will give arguments on why you should implement it on your websites by pure self-interest
- I will end with pointers on how to support HTTPS by using the free Let’s Encrypt service
The post is aimed at creators of small web apps or websites who want to deeply understand the building parts. It will not go into the details how HTTPS works on a technical level, but instead give the reasons why it is important and useful.
As a website’s user: Why HTTPS is important
Visiting a conventional HTTP-website (non-HTTPS) poses many issues for the visiting user. I will focus on the most easy-to-understand ones.
Privacy Issue
With HTTP, the communication between the user and the website is visible to multiple parties. Most alarming, anyone connected to the same WiFi network as the user can see the full communication between him and the HTTP-website. This means:
- What the user sends to the website. This includes the URLs a user visits (= requests the content under the URL), e.g.
http://www.<website>.com/article-123orhttp://www.<website>.com/some-image.jpg. More terrifying, this also includes all data that is sent via form submissions, e.g. when the user is logging in (username & password!), or when he enters his credit card details to complete a purchase. - What the website is responding with. This means, he can see the exact same content that the original user sees, e.g. a bank account balance displayed.
It is not hard to track HTTP communication within a WiFi network. Using a free tool like Wireshark, an attacker can record the communication of a fellow WiFi-user in real-time. If you don’t believe me, try it yourself (but of course in your own network, tracking your own devices. Anything else is illegal!). Relevant links to achieve it are here and here.
Some situations come to mind where HTTP becomes a big issue: If you are connected to an open WiFi like in a café, anyone in the same store could track what you are doing on your laptop/phone/tablet. Or at work - do you want your employer or your co-workers to be able to track what sites you are visiting? Probably not.
Unfortunately, even with HTTPS, anyone in the same WiFi can (most of the time) track the domains you are visiting. This does only affect the domain, not the path - so, if a user was visiting www.somesite.com/super/secret, people could track that www.somesite.com was visited, but not the part after the slash ("/"). But at the least, the exact path and the actual communication content are safe.
Integrity Issue
Another big problem with an HTTP website besides the privacy aspect: The website’s integrity is at stake. What does that mean? A third party sitting in between the user and the website can freely modify the communication, so that the website looks and behaves differently from how it is intended by the website’s owner. For example, the third party could provide you with a fake “gmail.com” website. There, the login field does not actually send the login data to Google, but to the third party’s own server. Who could then login into your Gmail. And the user will not notice that “gmail.com” was faked.
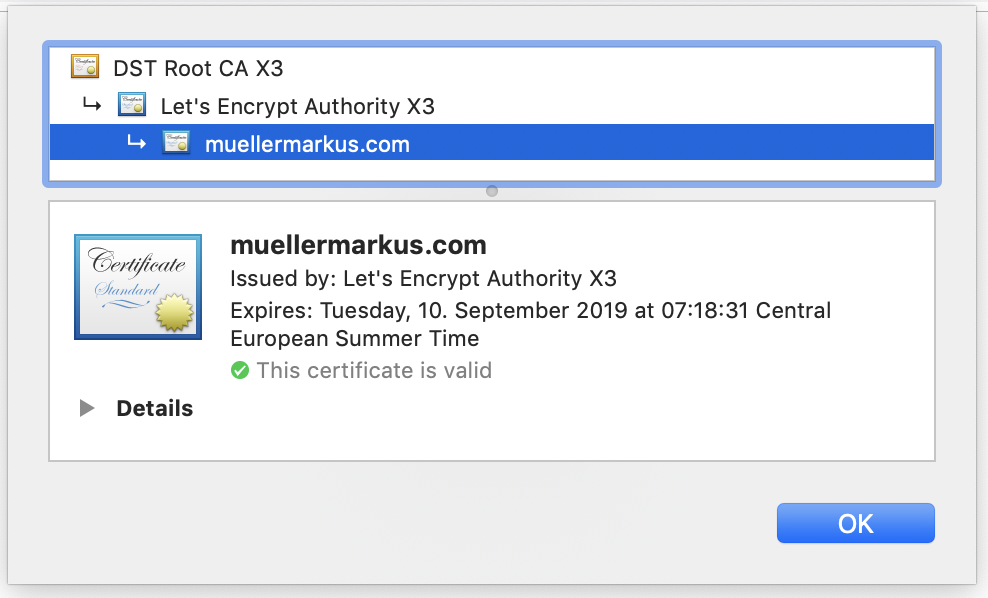
With HTTPS, in order to send traffic to the user under the “gmail.com” domain, the third party would need to obtain a valid SSL-certificate for the “gmail.com” domain, and sign the content using the certificate. SSL-certificates get issued by special trusted SSL certificate authorities (CAs), like Let’s Encrypt, or Digicert. Companies like Google and Amazon have also become certified as CAs and can issue valid SSL certificates on their own. CAs only issue SSL certificates to websites that have proven possession of the respective domain. There are different ways to do this - the one described at the end of this article is fully automatic.
You can view the issuing CA, e.g. by clicking on the lock in the address bar in Chrome. Here is how it looks for this website:
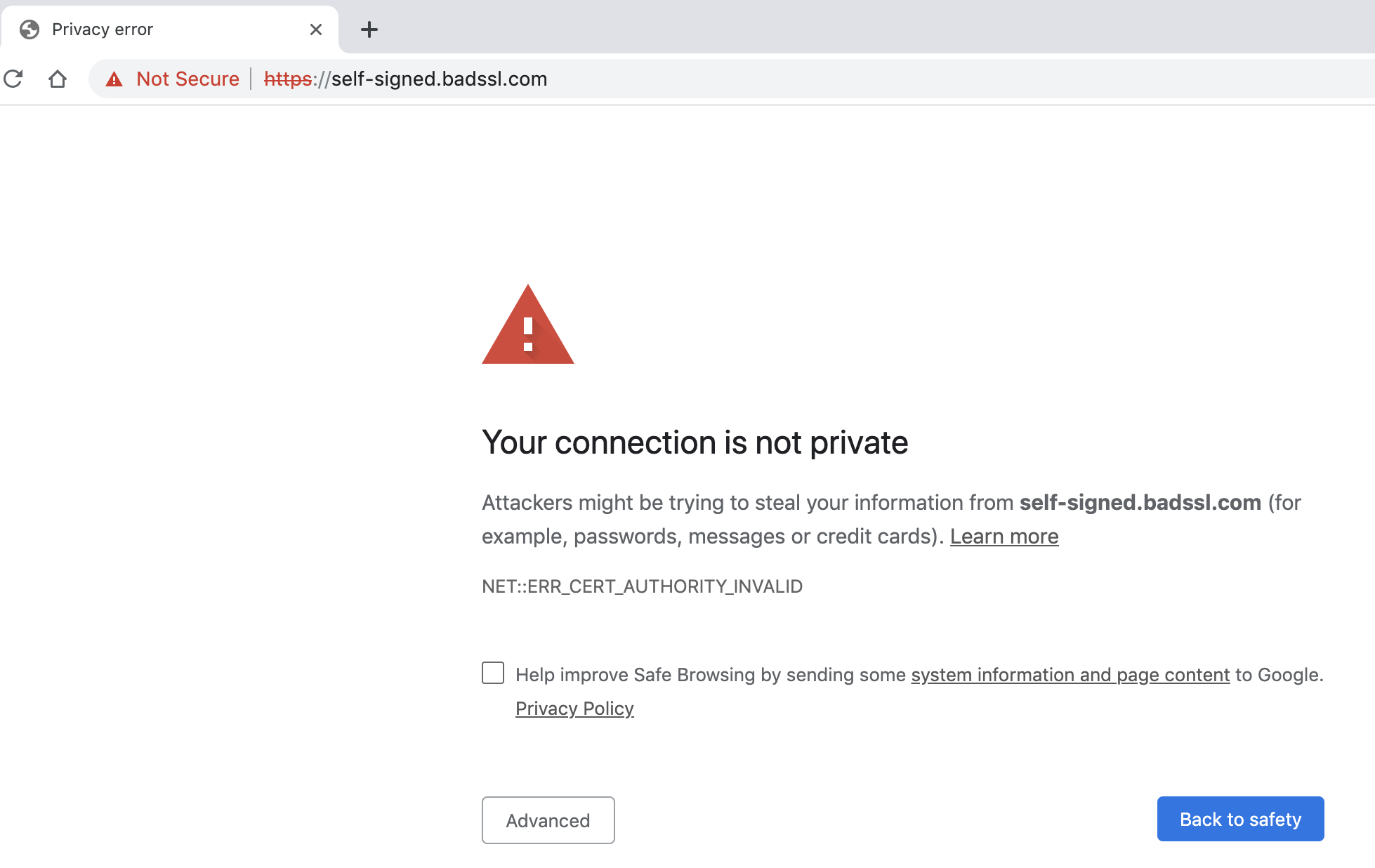
A third party other than the original domain owner does not have any chance to inject its own content, because browsers check that the website was signed with the valid certificate. If not, they will show an error and not display the website, e.g. like this:
Not all sites that support HTTPS are HTTPS-only (& how to always use the HTTPS-version as a user)
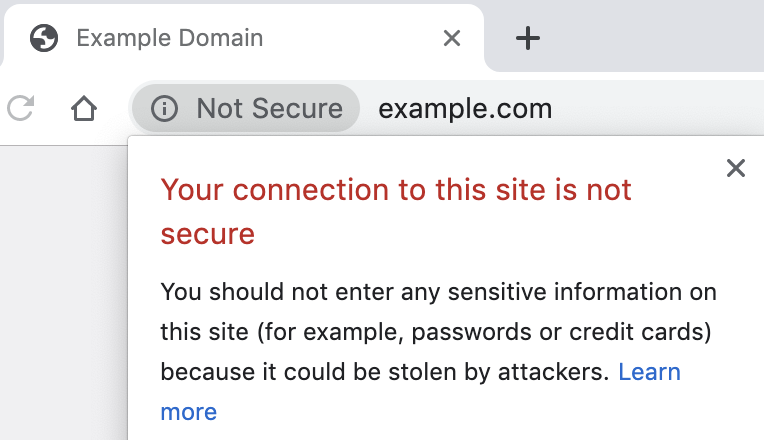
Please note: Not all sites that support HTTPS enforce HTTPS. For example, example.com is available via HTTP on http://example.com, and via HTTPS on https://example.com. Here the respective screenshots:
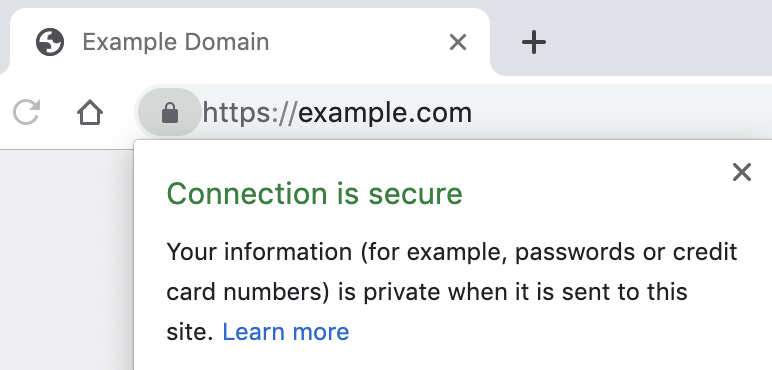
Websites need to actively redirect you to the HTTPS-version when accessing it via http:// - most websites do this, and all websites should do it. To be on the safe site as a user, you can use the HTTPS Everywhere extension that is available for most major browsers (except Safari & Microsoft Edge). This extension will redirect you to the HTTPS-version if the website itself does not (of course, this only works for sites that actually have an HTTPS-version).
As a website’s owner: Why you should implement HTTPS on pure self-interest
These were some big reasons for website users to use HTTPS-versions of websites. But if you are a website owner and not convinced that the additional security of your users is worth the hassle, there are some special reasons to convince you.
First, browsers are increasingly pushing for HTTPS and are marking HTTP-websites as not secure. Previously, the only difference when viewing HTTP and HTTPS website in a browser was that the HTTPS-website would have a “lock” indicator. Nowadays, in browsers like Chrome and Safari, the HTTP-version has a “Not Secure” text shown in the address bar. If the HTTP-website has input fields, this text will turn red to cause additional attention:
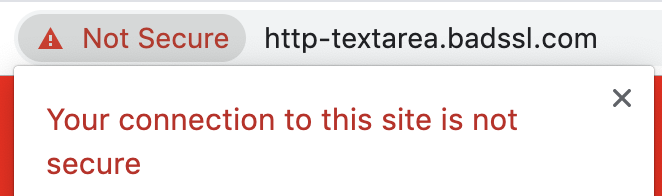
It is expected that browsers will put the squeeze tighter in the upcoming years, e.g. explicitly preventing form submittal on HTTP-websites, and placing the “Not Secure” warnings more prominently.
Second, since 2014, the availability of HTTPS has an impact of your site’s Google ranking. It is not clear how big the impact really is, but in times where SEO optimization has become a whole industry, not having HTTPS is just lazy.
How to support HTTPS for free using Let’s Encrypt
It has gotten really easy to add HTTPS to your website. Just a couple of years ago, you had to pay 50€/year or more for a SSL certificate. This all changed in 2014 with the emergence of Let’s Encrypt. Let’s Encrypt is a non-profit organization, founded by the Electronic Frontier Foundation and the Mozilla Foundation (amonst others). Main sponsors include companies like Google and Facebook. Let’s Encrypt is awesome. They issue free SSL certificates, in an easy and fast (mostly automated) way! So, there is no excuse in leaving out HTTPS when creating your website!
If you are using a popular web server like nginx or Apache, Let’s Encrypt’s Certbot is the easiest take for you. Their website provides tutorials like this one for nginx on Ubuntu 18.04 LTS (bionic). This tutorial is the one you would use if you followed my previous post “How to deploy a Python Flask application to the web with Google Cloud Platform - for free”.
If you are not running your website on a dedicated (virtual) machine, but on a shared host like Uberspace, a website builder like Jimdo or Squarespace, or some other platform like Netlify (that I use for this site), you need to look at their offerings. All the services I just mentioned offer HTTPS for free, you just might need to activate it.
Wrap-up
I hope this post provided a good overview on why HTTPS is important, both for a website’s users as for a website’s owners. At least since the rise of Let’s Encrypt, adding HTTPS to your website should be a “must-do” when setting up a new website or updating an existing one. I hope to have given the right pointers for you to implement HTTPS yourself. Encrypt the Web!
- My Favorite Shortcuts for VS Code
- Customizing my shell: From bash to zsh to fish
- JSON5: JSON with comments (and more!)
- jq: Analyzing JSON data on the command line
- Get Total Directory Size via Command Line
- Changing DNS server for Huawei LTE router
- Notes on Job & Career Development
- Adding full-text search to a static site (= no backend needed)
- Generating a random string on Linux & macOS
- Caddy web server: Why use it? How to use it?